Embedded System Security
The below table lists the popular security attacks, over the period.
| Sl.NO | Year of Attacks | Popular Attacks | Infected Devices |
|---|---|---|---|
| 1 | 2018 | Zwave Hack | 100 million |
| 2 | 2018 | Meltdown Spectre | Nearly Every Computer |
| 3 | 2017 | Krack | Nearly Every Wi-Fi |
| 4 | 2017 | Infineon ROCA | Chrome Book and windows devices created by Fujitsu, HP and Lenovo |
| 5 | 2017 | BlueBorne | 8.2 Billion Devices |
| 6 | 2017 | WannaCry | 300 K devices |
| 7 | 2016 | Mirai | 2.5 M devices |
| 8 | 2014 | HeartBleed | 200 K devices |
| 9 | 2010 | Stuxnet | 2.5M devices |
As per Symantec 2018 internet security threat report, the increase in percentage of internet security attack is 600.
Cost of security breach are not cheap
As per www.ncxgroup.com,
“A new survey by Altman Vilandrie & Company finds that nearly half of U.S. firms using an IoT network have been hit by a security breach, which can cost up to 13% of smaller companies´ annual revenue48% of organizations have experienced at least one IoT security breach.Nearly half of companies with an annual revenue above $2 billion estimated that the potential cost of one IoT breach is more than $20 million.”
Federal Trade Commission (FTC) on Security
As per FTC,
“For systems with significant risk, companies should implement a defense-in-depth approachcompanies should build security into their devices at the outset, rather than as an afterthought. As part of the security by design process, companies should consider:(1) conducting a privacy or security risk assessment; (2) minimizing the data they collect and retain; and (3) testing their security measures before launching their products. Second, with respect to personnel practices, companies should train all employees about good security, and ensure that security issues are addressed at the appropriate level of responsibility within the organization”
Defense-In-Depth
Defence-in-depth demands,
Security Needs
OEM Perspective
End User Perspective
Service Provider Perspectiv
Though it is everyone responsibility, OEMs brand will be seriously harmed in all these unsecure environments. So, it is the OEM's responsibility to address them all.
Achieving Security
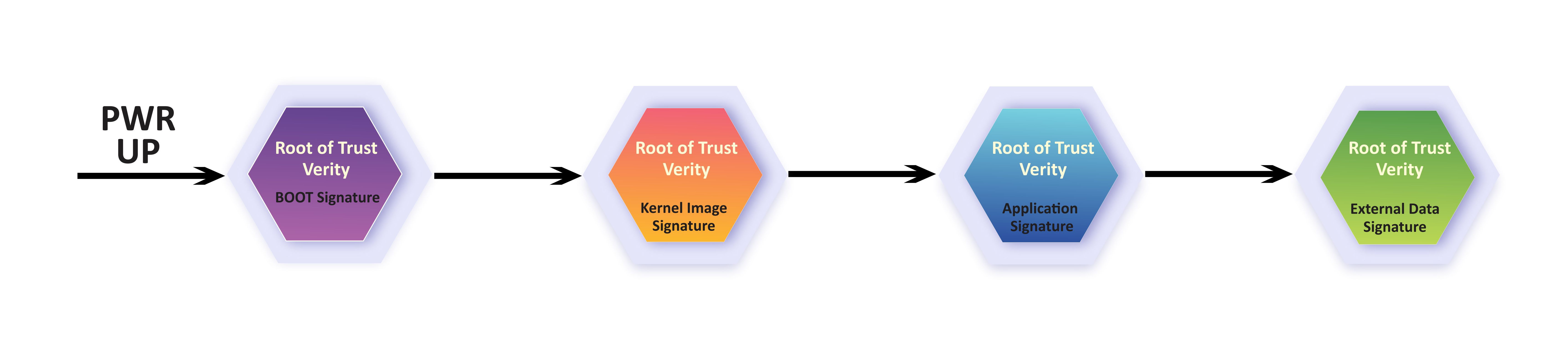
Chain of Trust
Chain of trust is a process which makes sure the genuine firmware, software, and Applications are being executed in the system. Chain of trust is established by validating each component of the software from the end entity up to the root certificate
Secure Key Storage
Complete security is built around the private key. If the private keys are compromised, then the security for the entire system breaks. Storing keys in a nonsecure medium is dangerous.
Secure FOTA
Complete security is built around the private key. If the private keys are compromised, then the security for the entire system breaks. Storing keys in a nonsecure medium is dangerous.In the connected devices ecosystem firmware can be updated remotely over the air for new feature, or more importantly to correct the compromised/corrupted firmware, however, to avoid the problem of malicious updates, FOTA itself needs to be secure.
The firmware package and firmware update communication channel need to be
Secure Data Storage
Unauthorized access to critical device data may spoil the brand name of OEM and may lead to significant revenue loss. Secure data storage applies to data that stored in the embedded device.
The firmware package and firmware update communication channel need to be
Secure Data Communication
The data communication by the device with any other connected device needs to be secure. Secure communication is that two entities are communicating and do not want a third entity to listen in.
Secure CAN Communication
Data communication by the device over the CAN interface needs to be secure. There may be multiple ECUs on the CAN bus with untrusted data. The system should listen only to the configured messages. System responding for unintended messages may avoid the intended use of the system.Data Security over CAN be achieved by
Inter vehicle Communication:
Secure Software Development
Software developed without any standard may lead to software bugs, which intern will lead to a sever security issues. E.g. HeartBleed issue.Developed software needs to take care of all the security vulnerabilities and should be as per the industry coding standards (e.g. CERT) defined for safe and secure code.
Tamper Detection
Tampering is one of the security issues in automotive electronic devices, the following are the tempering types:
Devices shall have inbuilt mechanism to detect these tampers and give alerts to vehicle owner.
ALTEN GT has very good expertise in Embedded Systems Security. ALTEN GT has developed both Hardware and Software Security features in Automotive Body Control Module, Telematic System and Vehicle Tracking Systems. ALTEN GT provides services in Design and Development of Automotive Systems with all latest security features.
Hardware security protection:
Secure Hardware design and validation support for
Software security protection:
Secure Software design and development support for
